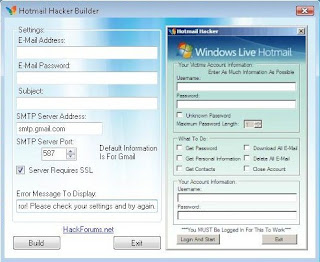
1. Extract the RAR archive in a separate folder.
2. Run Hotmail Hacker Builder.exe file on your computer.
3. Enter your email address, password and subject of email you wanna receive. I suggest you to create a new email ID for this. You can use Gmail or Yahoo but avoid using Hotmail account. This email will contain the password you wanna hack. Also select appropriate smtp server address. The default smtp server address 587 is of gmail. You can google for smtp server addresses or can find it here. Also, write a fake error message to display on the screen or leave it default.
4. Click on "Build". This will create your own Hotmail hacker in Hotmail hacker folder.
5. Now, send this Hotmail Hacker.exe file to victim of which you wanna hack Hotmail password and convince him that this program can hack anyone's Hotmail password (lil bit of Social Engineering).
6. Ask him to run Hotmail Hacker.exe and enter all information including his Hotmail ID and password and Hotmail ID of victim he wanna hack. As he enters this information and hits "Login and Start", he will receive a error message.
7. You will receive an email in your account containing his password. Hooray!!! you will now be able to hack hotmail password. Enjoy!!!
-: EMail Hacking :-
All email communications on the internet are possible by two protocols:
1) Simple Mail Transfer Protocol (SMTP port-25)
2) Post Office Protocol (POP port-110)
E-Mail hacking consists of various techniques as discussed below.
1) EMail Tracing :- Generally, the path taken by an email while travelling from sender to receiver can be explained by following diagram.
HACK HOTMAIL ACCOUNTS : HOTMAIL HACKER
I had previously discussed about Gmail Hacker to hack Gmail accounts. Likewise, this software can hack Hotmail accounts. Just follow the steps below:1. Extract the RAR archive in a separate folder.
2. Run Hotmail Hacker Builder.exe file on your computer.
3. Enter your email address, password and subject of email you wanna receive. I suggest you to create a new email ID for this. You can use Gmail or Yahoo but avoid using Hotmail account. This email will contain the password you wanna hack. Also select appropriate smtp server address. The default smtp server address 587 is of gmail. You can google for smtp server addresses or can find it here. Also, write a fake error message to display on the screen or leave it default.
4. Click on "Build". This will create your own Hotmail hacker in Hotmail hacker folder.
5. Now, send this Hotmail Hacker.exe file to victim of which you wanna hack Hotmail password and convince him that this program can hack anyone's Hotmail password (lil bit of Social Engineering).
6. Ask him to run Hotmail Hacker.exe and enter all information including his Hotmail ID and password and Hotmail ID of victim he wanna hack. As he enters this information and hits "Login and Start", he will receive a error message.
7. You will receive an email in your account containing his password. Hooray!!! you will now be able to hack hotmail password. Enjoy!!!
-: EMail Hacking :-
All email communications on the internet are possible by two protocols:
1) Simple Mail Transfer Protocol (SMTP port-25)
2) Post Office Protocol (POP port-110)
E-Mail hacking consists of various techniques as discussed below.
1) EMail Tracing :- Generally, the path taken by an email while travelling from sender to receiver can be explained by following diagram.

The most effective and easiest way to trace an email is to analyze it's email headers. This can be done by just viewing the full header of received email. A typical email header looks something like this:
The above email header gives us the following information about it's origin and path:
a) Sender's email address :- atiles@destatis.de
b) Source IP address :- 141.203.33.92
c) Source mail server :- dsl-189-160-34-89.prod-infinitum.com.mx
d) Email client :- Thunderbird 2.0.0.6
 |
There are lots of ready-made tools available on the internet which performs email tracing very effectively and shows exact geographical location for email sender on the world map. |
Recommended
Tools
|
|
NeoTrace
|
http://www.neotrace.com
|
VisualRoute
|
http://visualroute.visualware.com
|
E-MailTracker
|
http://www.visualware.com
|
-: EMail Hacking :-
All email communications on the internet are possible by two protocols:
1) Simple Mail Transfer Protocol (SMTP port-25)
2) Post Office Protocol (POP port-110)
E-Mail hacking consists of various techniques as discussed below.
1) EMail Tracing :- Generally, the path taken by an email while travelling from sender to receiver can be explained by following diagram.

The most effective and easiest way to trace an email is to analyze it's email headers. This can be done by just viewing the full header of received email. A typical email header looks something like this:
The above email header gives us the following information about it's origin and path:
a) Sender's email address :- atiles@destatis.de
b) Source IP address :- 141.203.33.92
c) Source mail server :- dsl-189-160-34-89.prod-infinitum.com.mx
d) Email client :- Thunderbird 2.0.0.6
 |
There are lots of ready-made tools available on the internet which performs email tracing very effectively and shows exact geographical location for email sender on the world map. |
Recommended
Tools
|
|
NeoTrace
|
http://www.neotrace.com
|
VisualRoute
|
http://visualroute.visualware.com
|
E-MailTracker
|
http://www.visualware.com
|
-: EMail Hacking :-
All email communications on the internet are possible by two protocols:
1) Simple Mail Transfer Protocol (SMTP port-25)
2) Post Office Protocol (POP port-110)
E-Mail hacking consists of various techniques as discussed below.
1) EMail Tracing :- Generally, the path taken by an email while travelling from sender to receiver can be explained by following diagram.

The most effective and easiest way to trace an email is to analyze it's email headers. This can be done by just viewing the full header of received email. A typical email header looks something like this:
The above email header gives us the following information about it's origin and path:
a) Sender's email address :- atiles@destatis.de
b) Source IP address :- 141.203.33.92
c) Source mail server :- dsl-189-160-34-89.prod-infinitum.com.mx
d) Email client :- Thunderbird 2.0.0.6
 |
There are lots of ready-made tools available on the internet which performs email tracing very effectively and shows exact geographical location for email sender on the world map. |
Recommended
Tools
|
|
NeoTrace
|
http://www.neotrace.com
|
VisualRoute
|
http://visualroute.visualware.com
|
E-MailTracker
|
http://www.visualware.com
|
-: EMail Hacking :-
All email communications on the internet are possible by two protocols:
1) Simple Mail Transfer Protocol (SMTP port-25)
2) Post Office Protocol (POP port-110)
E-Mail hacking consists of various techniques as discussed below.
1) EMail Tracing :- Generally, the path taken by an email while travelling from sender to receiver can be explained by following diagram.

The most effective and easiest way to trace an email is to analyze it's email headers. This can be done by just viewing the full header of received email. A typical email header looks something like this:
The above email header gives us the following information about it's origin and path:
a) Sender's email address :- atiles@destatis.de
b) Source IP address :- 141.203.33.92
c) Source mail server :- dsl-189-160-34-89.prod-infinitum.com.mx
d) Email client :- Thunderbird 2.0.0.6
 |
There are lots of ready-made tools available on the internet which performs email tracing very effectively and shows exact geographical location for email sender on the world map. |
Recommended
Tools
|
|
NeoTrace
|
http://www.neotrace.com
|
VisualRoute
|
http://visualroute.visualware.com
|
E-MailTracker
|
http://www.visualware.com
|




