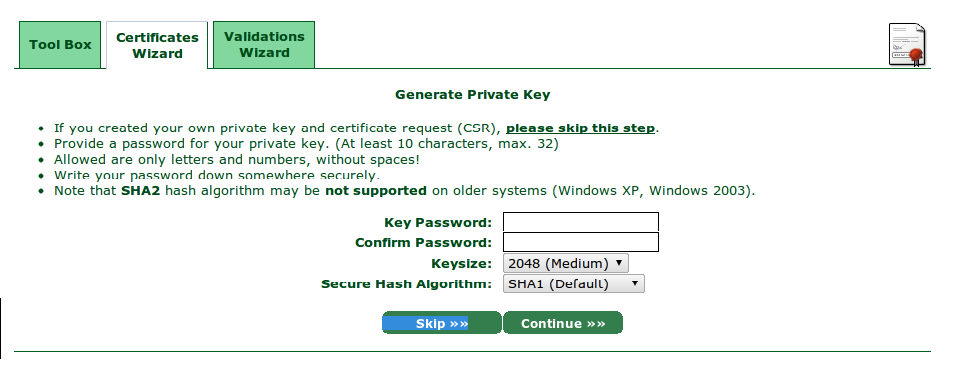
Have you ever wonder, how data recovery software works ? I mean,
everybody knows, when you delete files them are going to a special
folder
Recycle Bin, but what is happening when you
empty Recycle Bin ? To understand this we must first understand how data
are stored on storage devices e.g. hard drives. I don’t want to write a
very “technical” article, instead I will try to keep it as simple as I
can.
The most commonly file system formats used in modern Microsoft Windows based systems are
FAT (File Allocation Table) and
NTFS (New Technology File System). The
FAT and FAT32 is used predominantely by systems running earlier Windows
versions than Microsoft Windows XP for USB flash drives or memory
cards, while NTFS is preffered for newer versions of Windows : XP,
Vista, 7 or Windows Server 2008.
The smallest data unit is called a
sector and has on
Windows based systems hard disks a default size of 512 bytes but it’s
not used for direct space allocation as it is, instead the filesystem
use
multiple sectors to hold a data file. Them are called
clusters and are composed from 1 sector (512 B) to 128 sectors (64 KiB).
A) — a concentric magnetic field is called a
track;
B) — a geometrical sector;
C) — tracks are divided in
sectors
the smallest unit for holding data. Usually it can hold 512 bytes of
data. However, for storing a file, the smallest unit used is a cluster.
Sectors identification data as starting adress are written at the
beginning of the sector by the factory track-positioning data;
D) — multiple sectors , from 1 up to 128, forms a
cluster. In
the image above the cluster are composed by 4 sectors. If a sector is
512 bytes in size, then the cluster can hold 2048 bytes. For a file with
a size in 0-2000 bytes range, a cluster will be allocated. Always the
sectors numbers composing a cluster is an exponent of 2 : 1 sector, 2 ,4
, 8 and so on;
When a user format a hard drive under Windows, he must choice an
Allocation unit size in this range: 512B–64KB. If we have a lot of
small files in the computer and we are using big allocation unit size,
this result in a lot of wasted hard disk space. For example if we have a
lot of around 20-30KB size files and we allocate for them 64KB space
storage, the rest of unused space is wasted, however taking in
calculation actual hard disk sizes this is not something to concern us
too much like in the past when hard disk space was limited and
expensive.
In FAT architecture, the files and directories are stored in
Data Region. There is also
Directory Table
where are stored informations about files and folders, names,
extensions, attributes of the files, creation time, the adress of the
first cluster of the file thus pinpointing
which clusters are
used to store a certain file or directory, and finally the size of the
file or directory. Each entry associated with a file has 32 bytes in
size.
In NTFS architecture the Directory Table is replaced by the
Master File Table(MFT) containing informations about the files as : length of a file, location of the file,
permissions (not available for FAT). These informations are known as file
attributes and are stored in
so called
metadata files.
The
FAT Region is kind of table of content
containing informations about all clusters in a partition. It includes
multiple records about clusters e.g. : if it’s a free cluster, if it’s a
bad one, if it’s used and what is the next cluster in
the chain or if it’s the last cluster in the chain(or
EOC-End Of Chain) allocated to store a file.
The
Boot Sector containing the system
boot loader code is located in
Reserved Sectors. Another subsections as
File System Information Sector or
Backup Boot Sector are also placed there.
The first sector on a hard disk is the
Master Boot Record or
MBR
created concomitant with the creation of the first partition on hard
disk. For other un-partitioned storage devices the first sector is
called
Volume Boot Record,
VBR
shortly. This is the case also for a hard disk with several partitions,
the first sector in a partition is VBR while the first sector of the
whole hard disk is MBR.
The MBR contains a partition table with entries for each partition,
when a Windows system is booting, the MBR code loaded by the
bootstrapping firmware
contained within the ROM BIOS, search for a partition marked as active
and when it is found, it reads the VBR code from that partition passing
the control to the Windows loader(
NTLDR for all versions of
Windows up to Windows Server 2003). On the later Microsoft Windows
versions as Vista or Windows 7, NTLDR is replaced by the
Windows Boot Manager(BOOTMGR) which contain the boot loader code–
the bootstrap and the functionality is the same as the NTLDR.
Now on the subject, what is happening when a file is
deleted from Recycle Bin
and when a NTFS hard disk is formatted ? When you empty the Recycle
Bin, all the files from there are marked as deleted and unusable by the
operating system and their allocated space may be available to be
overwritten by another file. This is why you have a great chance to
recover a file if the recovery actions are taken immediately after
deletion. Older deleted files has more chances to be overwritten by the
new files we save on the hard disk and thus fewer chances to be fully
recovered.
In the case of hard disk formatting, the Master Boot Record and the Master File Table are erased but the
real data of the
files are still there on the hard disk being possible to recover them.
The format system offer two options, quick and full format with only
difference that the full formatting of a hard disk will check for “bad
sectors”, will flag it as unusable by the operating system and will try
to reallocate it with a sector that is keept as a “back-up” sector on
the hard disk. On every hard disk there is a bunch of sectors specially
reserved for replacing the eventually bad sectors.
However this is the theory, because when a formatting of a hard disk or a storage device is done, only
MFT and MBR(VBR) for NTFS or the
Directory Table
for FAT structure is erased but the files still exists, a software can
instruct the driver for a low level “bit-by-bit or better said
sector-by-sector” reading of the device looking for data files.
Consequently if you want to
truly delete your data,a special
software must be used the so called “disk scrubbers, shredders or disk
wipers”, able to overwrite all the sectors on hard disk with 0 character
or special bit patterns. Often such software has an option for
repetition of deletion for the most “paranoids” of users. Though I never
tested them, there is software that claims it can recover overwritten
data by instructing the hard disk driver to read low level
remanent magnetic fields
on a hard disk, that’s why some of the users preffer to wipe the hard
disk several times. However, in forensic laboratories this is
theoretically possible. If you sell or donate your old computer, old
laptop or you are keeping sensitive data on the computer and you are
afraid for it to be stolen, a disk wiper may interest you.
Let’s mention some good data recovery software :
iCare Data Recovery Software
It can run from an USB device, no need to install it in the computer
and does a pretty good job recovering in seconds lost data from hard
disks, memory cards, smart media, ipod and almost any storage device.
The recovered files for example photos can be previewed while the
searching for files continue. The program can helps if :
- Lost partitions or USB device not detected error;
- Drive not formatted error;
- Recover files from dynamic disk, RAID ;
- Bad MFT, bad MBR, bad partition table;
- Deleted files by viruses;
- Accidentally deleted or formatted hard disk or any other media storage;
When the program starts it present to the user
4 options, as follows :
- Lost Partition Recovery;
- Advanced Files Recovery;
- Deep Scan Recover, itb uses a special algorithm;
- Format recovery;
I’ve already mentioned that programs recover files and folders real quickly and with a big rate of success.
As a bonus for reading this article, you can have
iCare Data Recovery Software for free and this is why :
Was a Free license giveaway that must end in 25 May 2010, but when
I’ve tested the download link from the official site and the giveaway
license I’ve found on the Internet, I have had the pleasant surprise to
discover the free license still works.
The free license code is :
2K1XB2X964MPHOCJ8M1R6IJF0OVHFOFH
and the official download link is
here.
Grab it quickly while you can still have a 69,95$ worth software for free.
EASEUS Data Recovery Wizard
Offer a free edition of the software. It has an intuitive interface,
being very simple to use, recover from formatted disks, memory cards,
flash USB drives.
Recuva
From the creators of well known
CCleaner, it’s a
free
product with a portable version provided aswell. Restore deleted
emails, Word documents, iPod music, photos from a deleted or formatted
partition from your PC or from a memory card. A preview of any recovered
image is possible in the program window.
For disk wipe utilities can be mentioned :
Disk Wipe
Free software
doing very well its job. It uses several shredding algorithms and can
definitively erase hard disks, USB thumbs or memory cards.
Eraser
It can erase your hard disk according to the US Department of Defense
(DOD) standard to repete the data overwritten process with random
bytes, 3 or 7 times or the Gutmann recommendation of 35 times. It works
under all versions of Windows including Vista and Windows 7.
Freeraser
The same as previous, it eliminates all the possibilities to recover data from a processed storage device.
Disk Scrubber by MariusSoft
It has an affordable price, it’s a relatively new software. It can wipe the NTFS partitions of your hard disk.